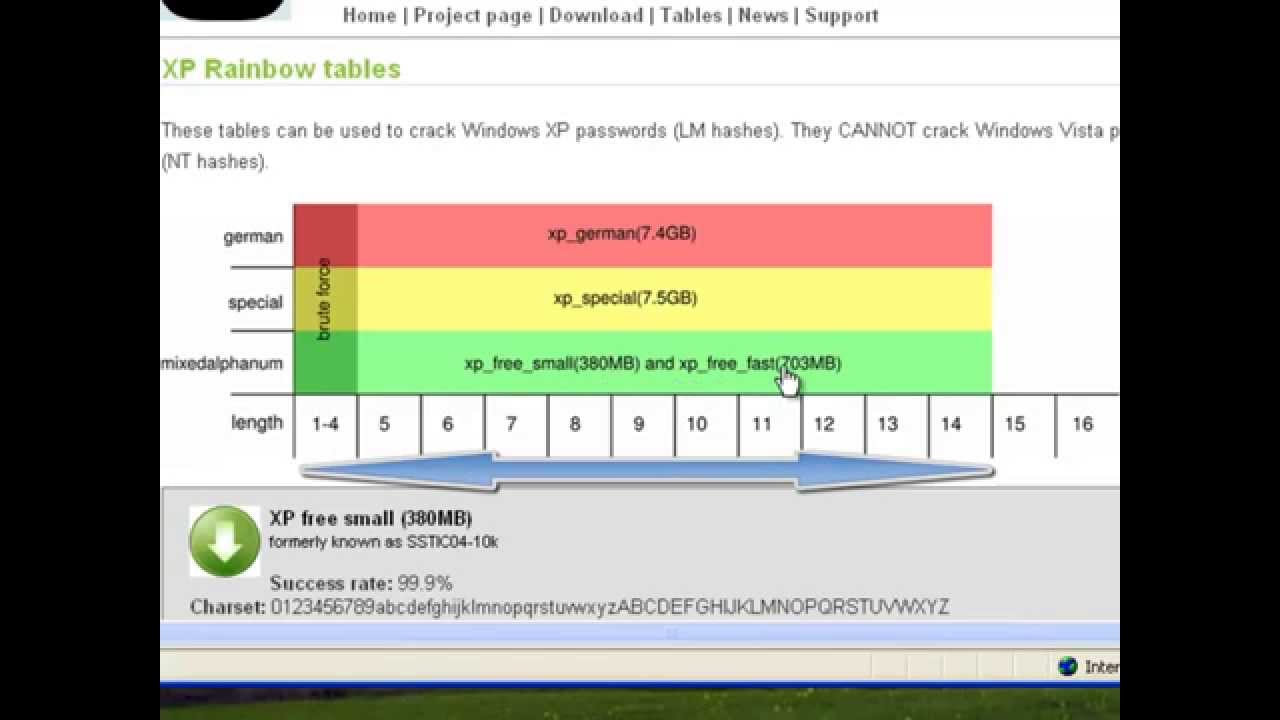
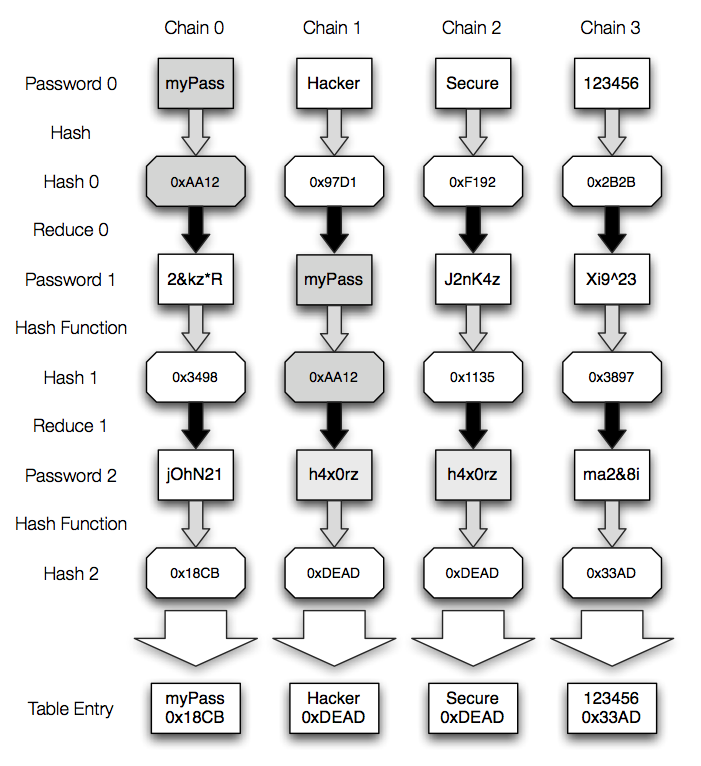
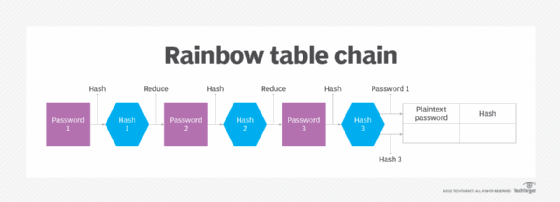
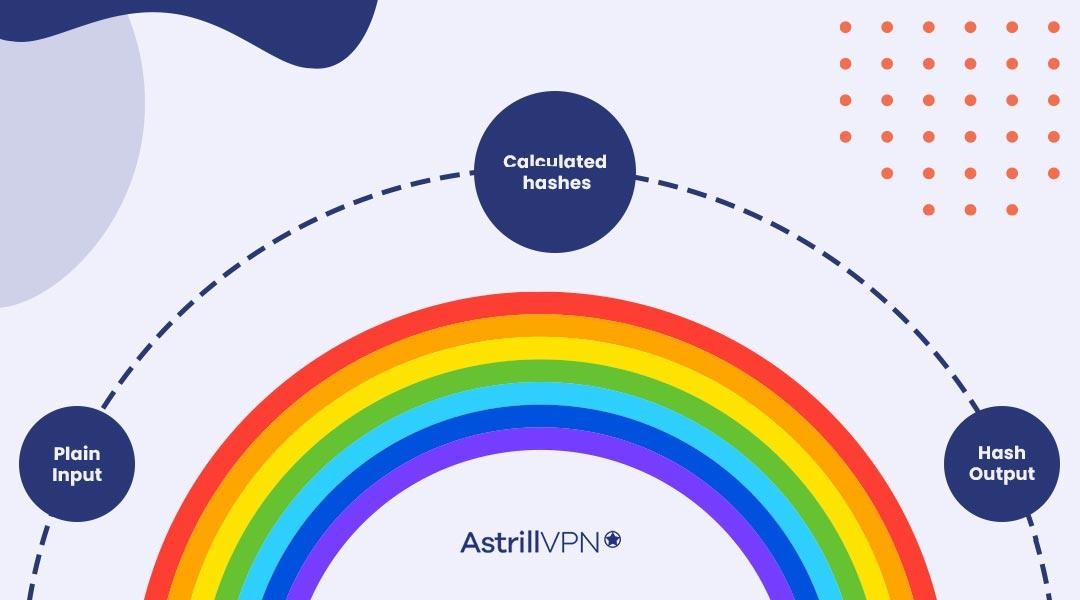
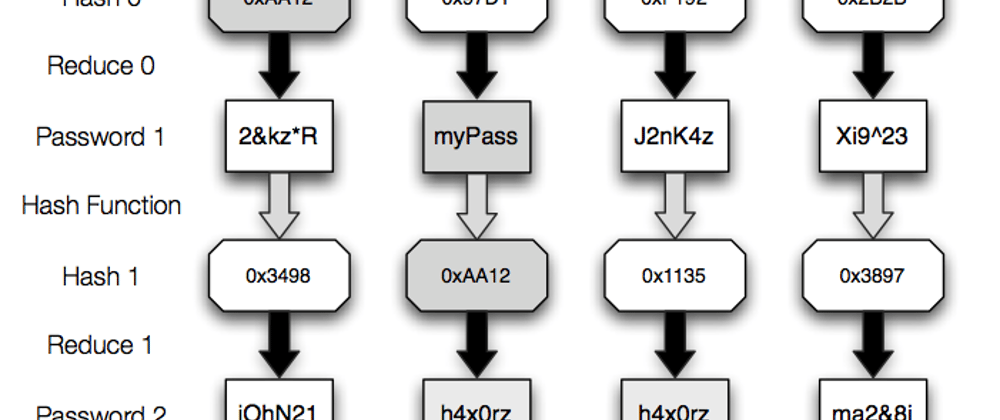
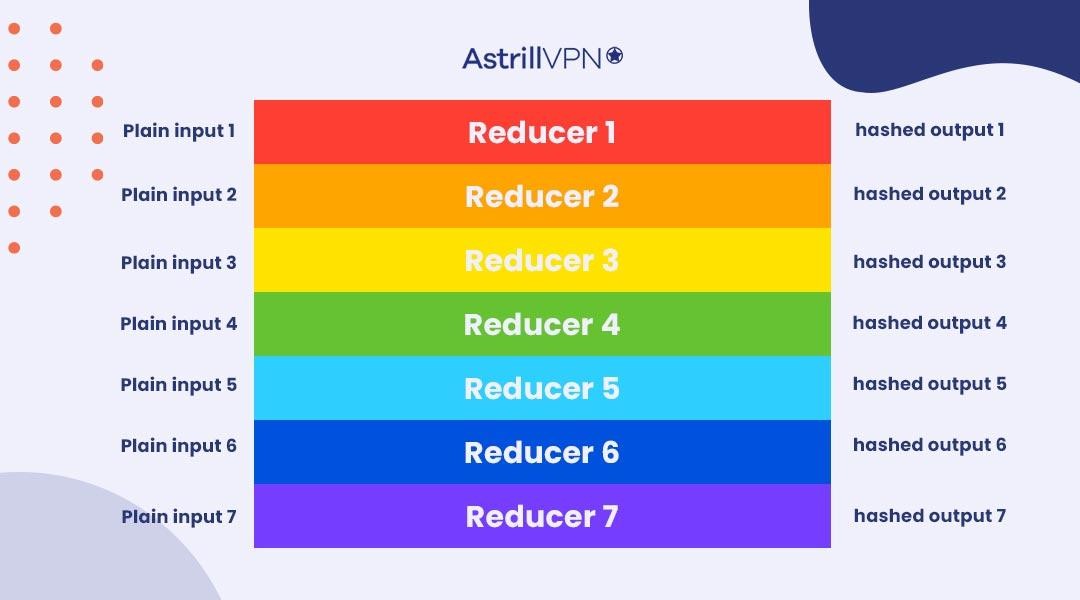
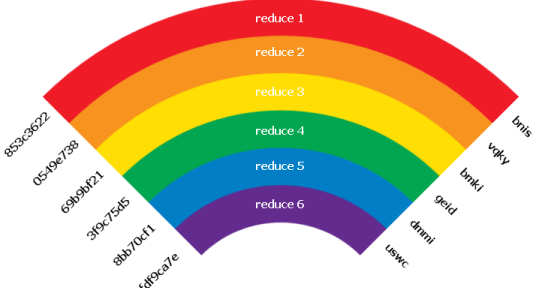
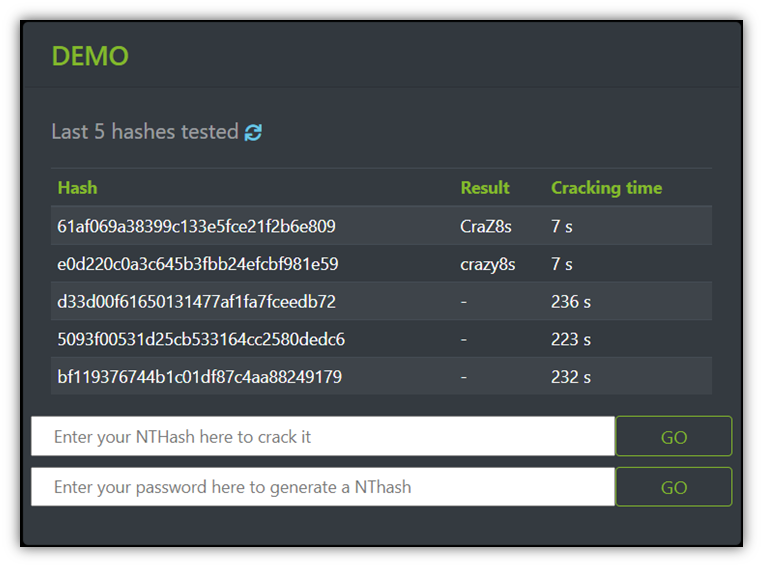
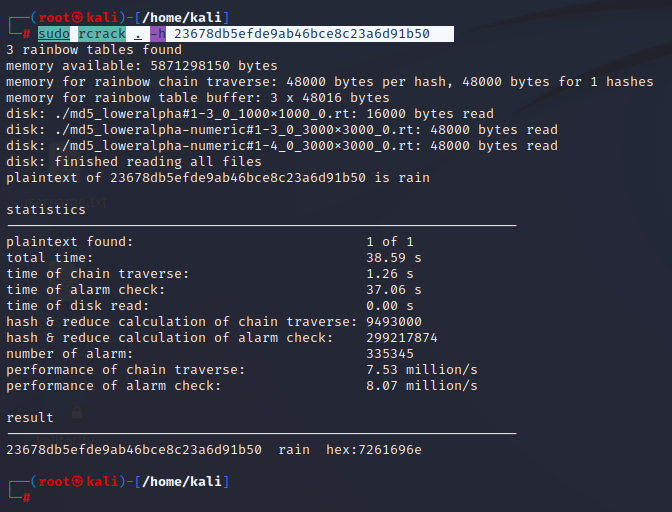
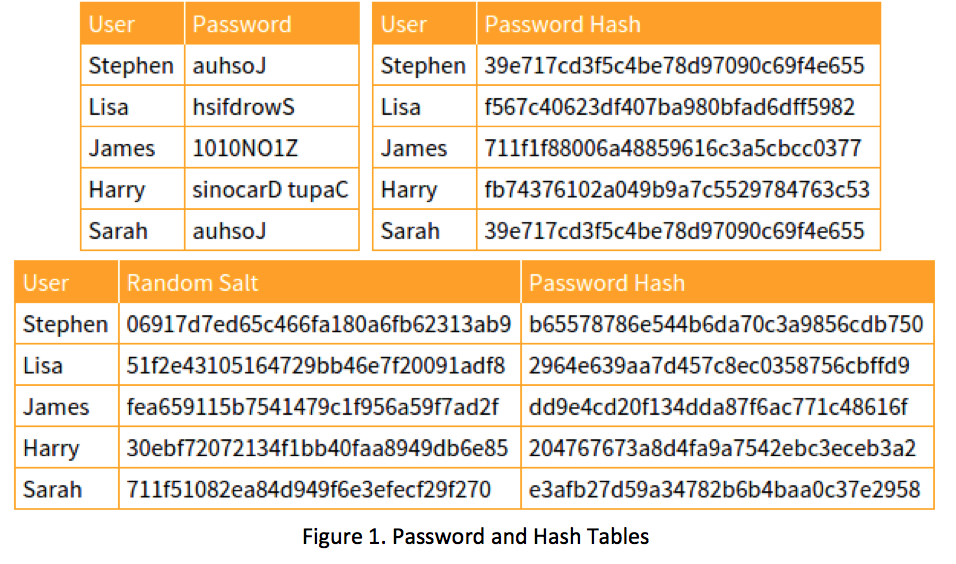
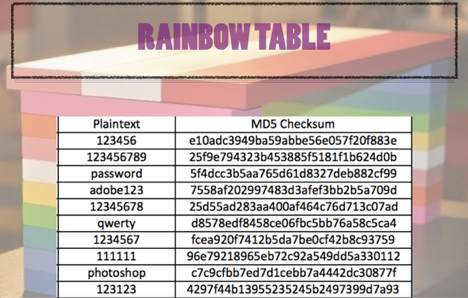
Whiz Security - Rainbow Table Attack A rainbow table attack is a type of hacking in which the attackers tries to use a rainbow hash table to crack the passwords stored in

I͛P͛h͛o͛n͛e͛G͛a͛l͛a͛x͛y͛M͛D͛ 10K͛ 🏴☠️ on X: "Rainbow table attack #attack #attacks #cyber #cybersecurity #cyberattack #hash #table #hashing #hac #hacks #hack #hacker #hacked #hacker #hackers #hacking #ddos #awareness #aware #safe #security ...